Sha1 Uses Which of the Following Bit Length Hashing Algorithms
Static string Hash string input using SHA1Managed sha1 new SHA1Managed var hash sha1ComputeHash EncodingUTF8GetBytes input. Foreach byte b in hash can be x2 if you want.
SHA1 uses which of the following bit length hashing algorithms.

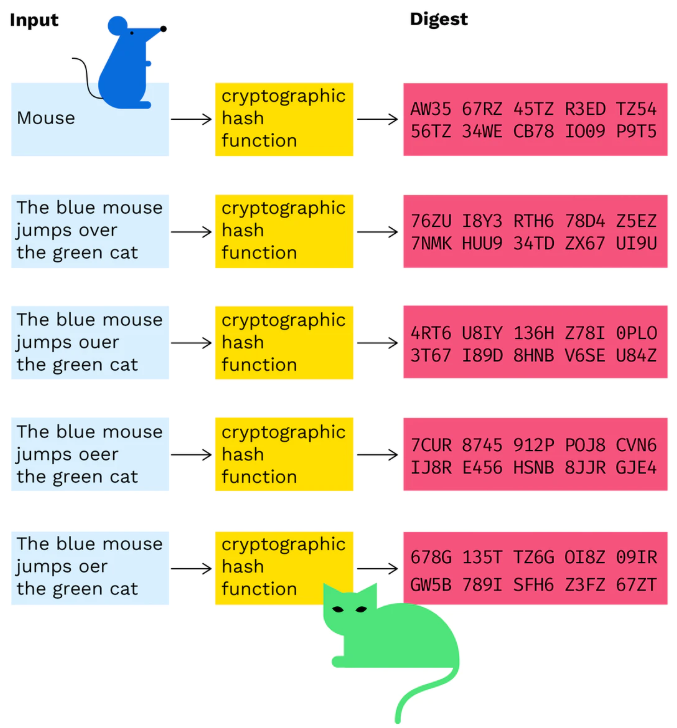
. The hash value therefore generated is known as a message digest which is typically rendered and produced as a hexadecimal number which is specifically 40 digits long. SHA-1 is a 160-bit hash and SHA-256 generates an almost-unique 256-bit 32-byte signature for a text. NIST Policy on Hash Functions.
This was designed by the National Security Agency NSA to be part of the Digital Signature Algorithm. Federal agencies should stop using SHA-1 for generating digital signatures generating time stamps and for other applications that require collision resistance. Uses 160 bits to encrypt the data.
Asked Feb 14 2019 in Computer Science Information Technology by heckert1965. SHA1 is the secure hash algorithmSHA. Identify the enumeration technique where attackers enumerate.
Here SHA-1 is a basic version of the hashing function and its close to the MD5 in nature which means SHA-1 has a shorter code resulting in less possibility for unique combinations whereas SHA-2 or SHA-256 makes a more extended code and offers more complex hash. SHA384 is the SHA that uses 384 bits to encrypt the data. Both SHA1 and SHA-1 refer to each other.
SHA-1 is widely used in various public-key cryptographic algorithms eg. Federal Information Processing Standard and was designed by the United States. For those who want a standard text formatting of the hash you can use something like the following.
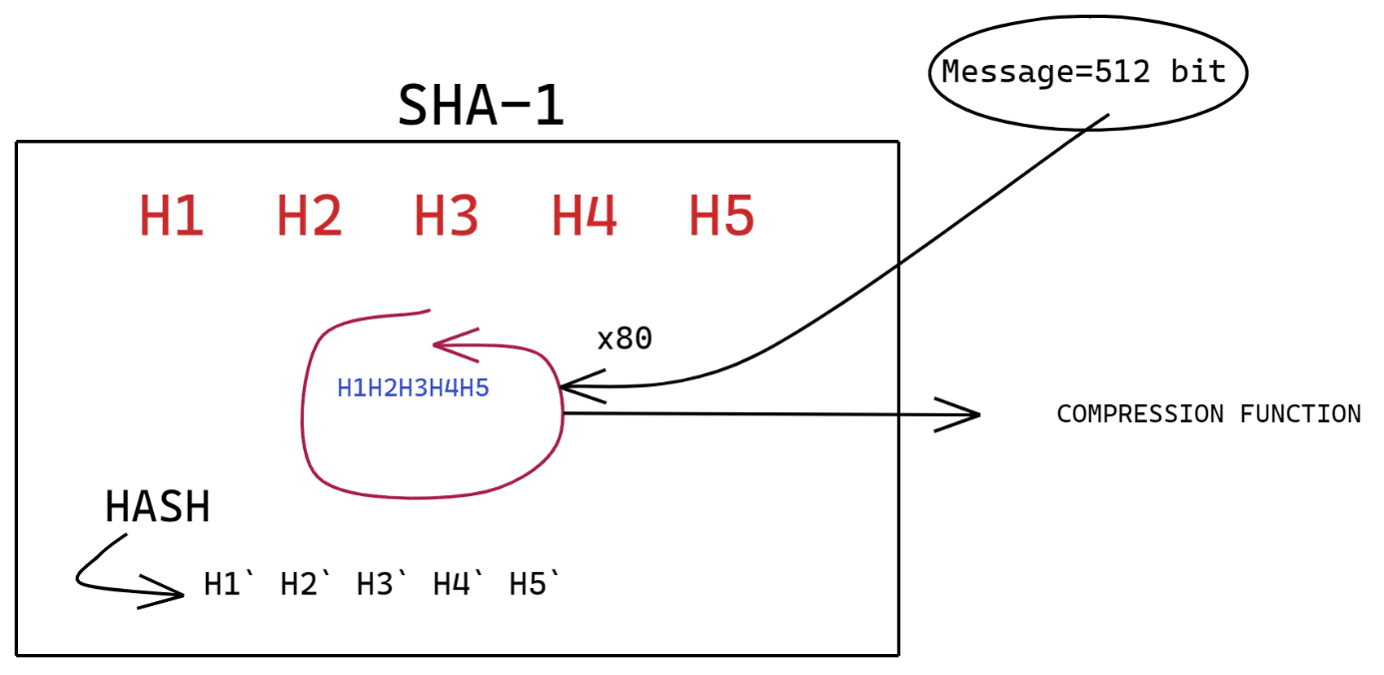
This algorithm generates a 160-bit hash value. Message 512 bit block Message 1 0000 size One bit of 1 following message Pad with 0s to within 64 bits of end of block Last 64 bits of last block get the size of the message in bits. Therefore we will disable the use of the following SHA-1 based DNSSEC algorithms.
For a long time SHA-1 hash algorithms are considered non-secure. It is a US. Only 160bit Only 128bit 128bit 160bit 192bit 224bit and 256bit 224bit 256bit 384bit and 512bit.
In Digital Signature Algorithm DSA 6. 11 rows It was withdrawn shortly after publication due to an undisclosed significant flaw and replaced by the slightly revised version SHA-1. Hash algorithms like MD5 and SHA are considered secure for creating digests because these hashing algorithms are designed to create a digest as strong as possible.
The MD5 algorithm produces 128-bit checksums and SHA produces 160-bit checksums. SHA stands for secure hashing algorithm. First the message is preprocessed.
Net Framework supports the following hash algorithms. SHA-1 is the first version of SHA and is the least secure version of SHA hashing algorithm. Verifying old digital signatures and time stamps generating and verifying hash.
This message digest is usually then rendered as a hexadecimal number which is 40 digits long. SHA-1 is known to have weaknesses and should only be used where required for compatibility purposes. SHA-256 also referred to as SHA-2 is a newer version of SHA and uses 256-bit checksum.
Secure Hash Algorithm 1 or SHA1. SHS describes the following algorithms. SHA-256 is one of the successor and strongest hash functions to SHA-1.
The SHA-256 hashing algorithm is part of the SHA-2 family. The Secure Hash Algorithm takes a message of less than 2 64 bits in length and produces a 160-bit message digest which is designed so that it should be computationaly expensive to find a text which matches a given hash. This hash value is known as a message digest.
SHA-1 SHA-160 SHA-256 SHA-385 and SHA-512 where the number is the length of the hash H in bits. Hashing using the MD5 Hash or SHA Hash has a standard of certainty even higher than that of DNA evidence. The bit-length is insufficient for the current computer power.
MD5 is an algorithm gets a input of length and output digestedMD5 uses 128 bits to encrypt the data. In January 2020 researchers described an attack that has the potential for dangerous and far-reaching consequences in the DNS ecosystem. SHA-1 Algorithm Pre-process the message pad and end with size.
SHA-1 or Secure Hash Algorithm 1 is a cryptographic hash function which takes an input and produces a 160-bit 20-byte hash value. SHA-1 is created in 1995 as the successor of the SHA-0. Cryptographic weaknesses were discovered in SHA-1 and the.
In the field of cryptography and crypt analytics the SHA-1 algorithm is a crypt-formatted hash function that is used to take a smaller input and produces a string that is 160 bits also known as 20-byte hash value long. SHA-1 and SHA-256 are two different versions of that algorithm. The following buffer variables are used by SHA-1.
Federal agencies may use SHA-1 for the following applications. Moreover SHA-1 developed by the US government offers 20 bytes 160-bit hash values which are. Asked Jun 30 2016 in Criminal Justice by Cheetos.
They differ in both constructions and in bit-length of the signature. Var sb new StringBuilder hashLength 2. SHA1 hash algorithm is generally used in security and data integrity applications.
This algorithm was developed for use with DSA Digital Signature Algorithm or DSS Digital Signature Standard. Identify the enumeration technique where attackers enumerate sensitive information such as encryption and hashing algorithm authentication type key. The bit 1 is appended to the message followed by appending zero or more 0 bits so that the total length of the message is congruent to 448 modulo 512.
In this report only SHA-1 SHA-160 is consid-ered. We all are in an era where information transfer on internet is very common and without that our communication cant be done properlyIt becomes very easy to share any file or message on the. Ie if you have a hash for document A HA it is difficult to find a document B which has the same hash and even more.
A 160-bit hash function which resembles the earlier MD5 algorithm. SHA256 is the SHA that uses 256 bits to encrypt the data. SHA1 is in a hash or message digest algorithm where it generates 160-bit unique value from the input data.
For new code we recommend the SHA-2 family of hashes. Secure Hash Standard SHS 7. H0 0x67452301 H1 0xEFCDAB89 H2 0x98BADCFE H3 0x10325476 H4 0xC3D2E1F0.
Sha 1 Sha 2 Sha 256 Know The Difference
String Hashing Algorithm Compendium Sobyte

What Is The Hashing Function And Can It Become Vulnerable Venafi
Cryptographic Hash Algorithms An Introduction Blockchain Technology

Passwords And Hacking The Jargon Of Hashing Salting And Sha 2 Explained Data And Computer Security The Guardian
Hashing Algorithms An In Depth Guide To Understanding Hash Functions Appsealing

Sha1 Based Hashing Algorithm The Hash Function Is A Deterministic By Relictum Pro Medium

What Is The Hashing Function And Can It Become Vulnerable Venafi

Why Is Hashing Your Top Priority For Data Security

What Is Sha Sha 1 Sha 2 Encryption Consulting
Hashing Vs Encryption What Are The Difference
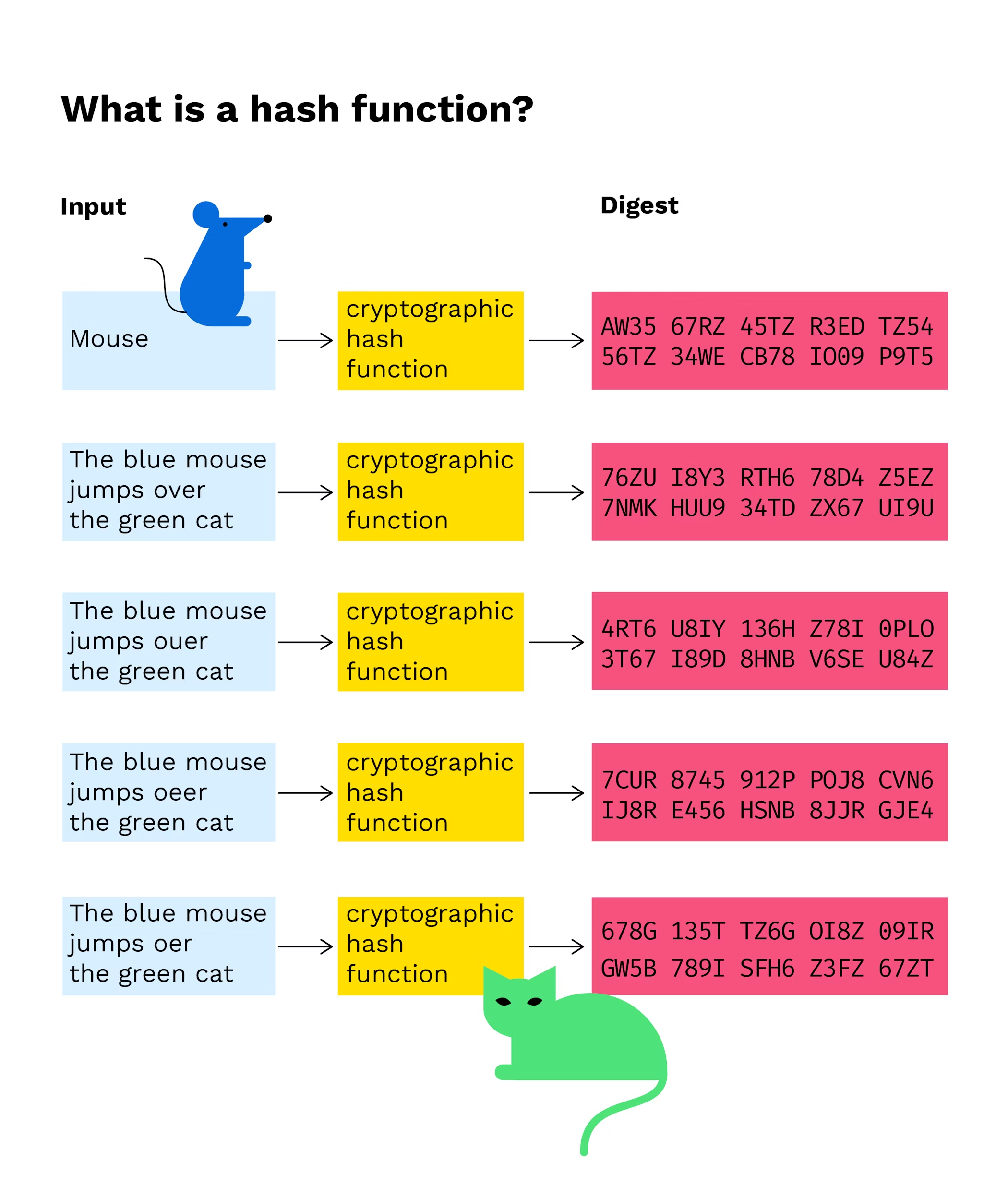
What Is A Hash Function In A Blockchain Transaction Bitpanda Academy
What Is The Best Hashing Algorithm

Secure Hash Algorithms Brilliant Math Science Wiki
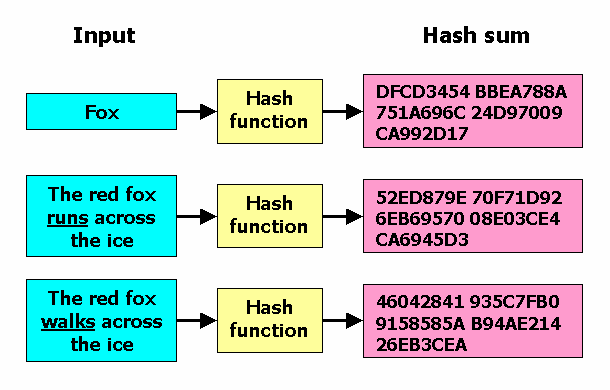
Md5 Vs Sha 1 Vs Sha 2 Which Is The Most Secure Encryption Hash And How

What Is A Hashing Algorithm And How Does It Work Crosstower

Pin By Bill Chaney On Techinfo Cheat Sheet Networking Infographic Networking Basics Computer Network

Cryptographic Hash Algorithms An Introduction Blockchain Technology
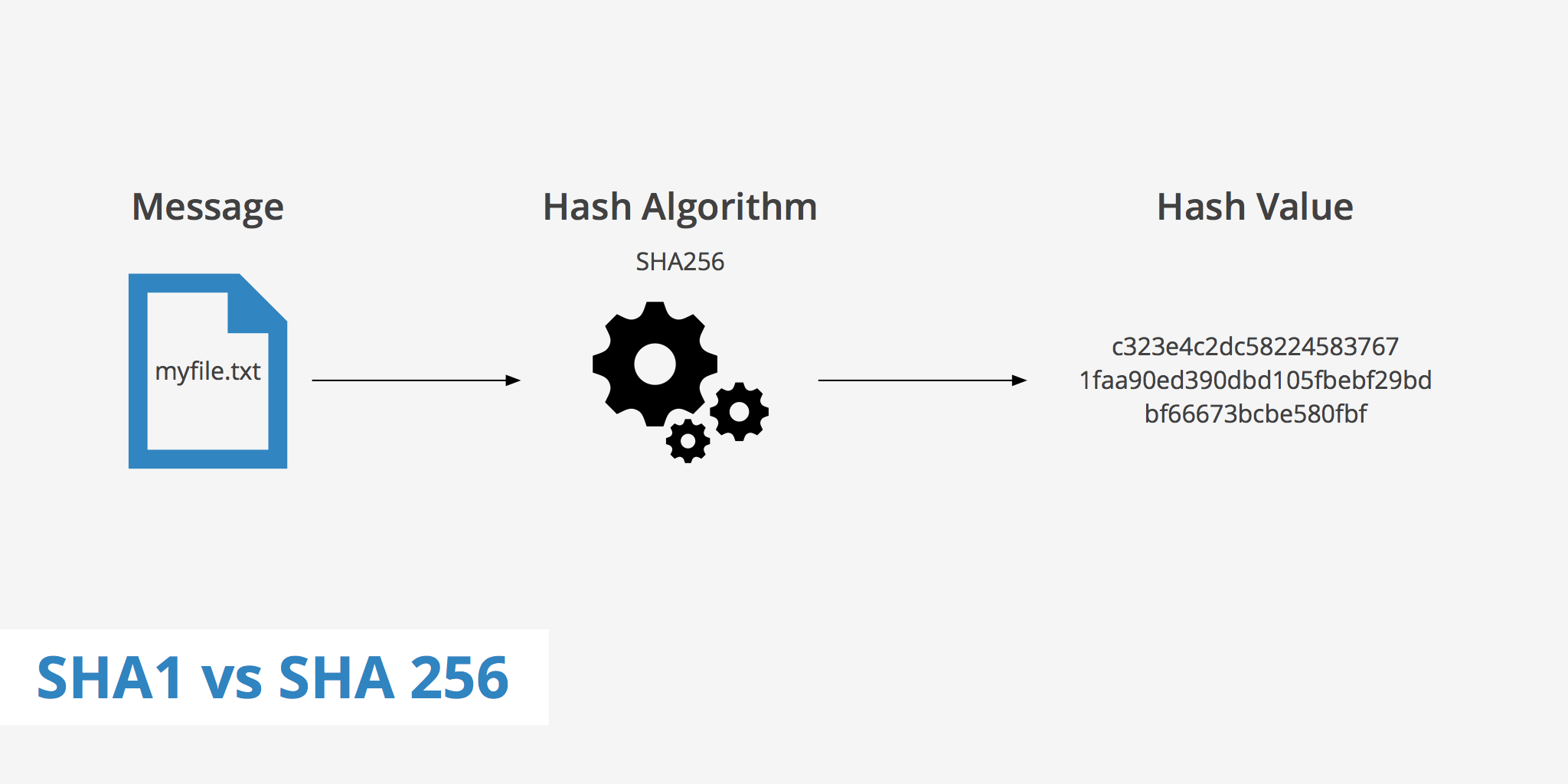

Comments
Post a Comment